Checking Windows Firewall for blocked ports
If you have Windows Firewall enabled then chances are that eventually you are going to find that it will be blocking one or more ports required by your applications. Checking Windows Firewall for blocked ports will help you troubleshoot your issues.
To check if Windows Firewall is blocking a port(s) that your machine is trying to communicate, follow the steps below…
Pre-Check: What ports is the machine listening on?
First off, let’s check if your server is even listening on the specific port you think might be being blocked by Windows Firewall.
To check what ports a Windows machine is listening on, do the following:
- Launch Command Prompt
- Run
netstat -a -n - Check to see if the specific port is listed
- If it is, then it means that the server is listening on that port
- If it isn’t, then it means that port is not being used, so either the application in question is not running or in fact the application isn’t actually using that port at all
Option 1: Checking Windows Firewall for blocked ports via Windows Firewall Logs
The first way to check what ports Windows Firewall is blocking is to use the Windows Firewall logs. To do this, follow these steps:
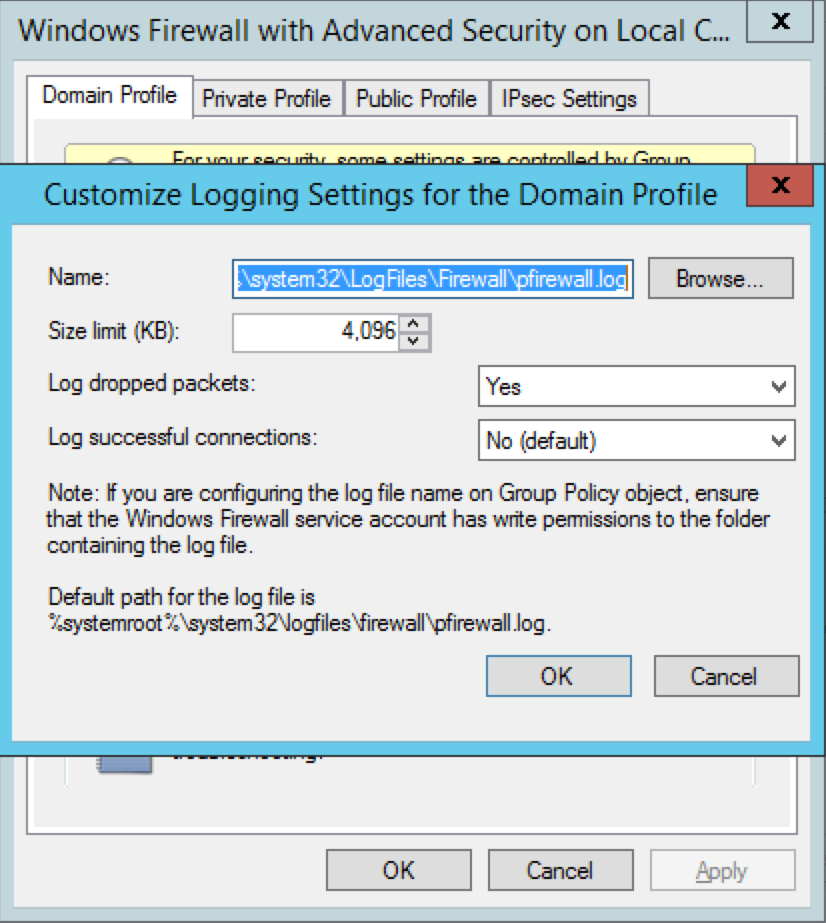
- Enable Dropped Packets Logging
- Start >> Control Panel >> Administrative Tools >> Windows Firewall with Advanced Settings
- From the Actions pane (right-pane) click on Properties
- Select the appropriate firewall profile (Domain, Private or Public). Alternatively, enable logging on all three profiles
- Click the Customise button under the Logging section
- Change the Log Dropped Packets option to Yes
- Take note of the file path to where the logs will be stored
- Click OK to enable logging (see screenshot below)
- Navigate to the logging file path (as per file location in Logging settings above)
- Check the log file for any blocked ports
Option 2: Checking Windows Firewall for blocked ports via Command Line
You can also get a list of the active listening and the blocked ports by using the Windows Firewall commands through command prompt. This documented below:
To get a list of the Windows Firewall blocked ports and active ports run:
netsh firewall show state
To get a list of the Windows Firewall configuration run:
netsh firewall show config
Note: The netsh firewall set of commands have been depreciated (although they still work on Windows 2012 R2). The new set of commands are netsh advfirewall firewall.
At this stage I haven’t been able to work out how to get a list of the blocked ports using these new set of commands and hence I still use the old commands.
For more information about netsh advfirewall firewall commands, see the following post >>> (How to use netsh advfirewall firewall set of commands)[https://support.microsoft.com/en-us/kb/947709].
How To – Allow ICMP ping through the Windows Firewall
If you are looking for how to allow ICMP ping through the Windows Firewall (as this is blocked by default on Windows 2008+ server operating systems), then follow the steps in the following article >>> How To – Allow ping through the Windows Firewall.
Checking if other firewalls are blocking ports
What if it isn’t Windows firewall that is blocking your port but rather another external firewall? How do we check if another firewall is blocking any ports?
The following command will show you if possibly any other firewalls are blocking any ports for your application. How it works is pretty simply, if nothing is return it means no ports are currently being blocked. If something is returned, then possibly that is the port that might be blocked. This is a good starting point to check firewall logs on the actual firewall to see if it is being blocked or not.
netstat -ano | findstr -i SYN_SENT
Linux? Although this is a Windows article, in the event that you need to find out if firewalls are blocking any ports on your linux machines, you can run the following command:
netstat -ano | grep -i SYN_SENT
For more information about these commands, take a look at this excellent article by Ather Beg – Identifying and Troubleshooting Firewall Access Issues
Hope this helps!. Let me know if you have any questions or comments below.
I have application listening to the port 10.x.x.x 443 i am able to see TCP listening to that IP and port. This application installed in my Windows 10 Hyper-V. PCF dev. But I am not able telnet this ip address with specific port. How to check what is blocking me to telnet this port on this IP address
hello luca ,how to detemine a open TCP port like 111 or 6080 or 4750… is safe for the server,(i mean it would not help the hacker to attack our server)thx a lot. 🙂
I don’t see the required port is listening (i need port 443 to be opened) how can I open port in my server running MS Windows 2008 R2?
why are my bookmarks being blocked